Widespread application of modern technologies has opened the door to cyber-attacks and potential security breaches, as more individuals and agencies rely on certain technologies, this leaves them vulnerable, today we explore the communications industry best security practices that can negate these modern threats.
When technological security is involved, strong encryption is a best practice solution to negating what is known as ‘bruteforce’ cyber attacks. A brute force attack is a hacking method that uses trial and error to crack passwords, utilizing known or ‘leaked’ credentials. This serves as the most common tactic in order to access individual accounts or organization’s systems and is seen as the most basic attack. However there are various different attacks such as: denial of service (more commonly known as DDoS), phishing, and MiTM or man-in-the-middle attacks.
There are over 2,220 cyber attacks everyday of varying complexity, meaning there’s over 800,000 cyber attacks per year, or one attack every 39 seconds.
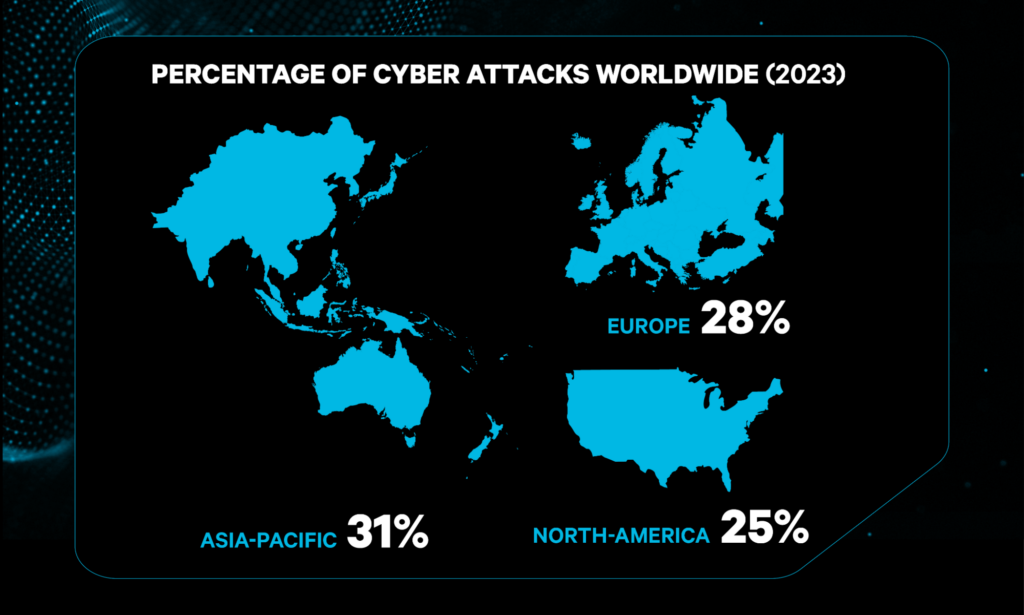
Cyber security is a geopolitical problem, it concerns all areas of the world. As of 2023, the Asia-Pacific region was the most targeted by cyberattacks, representing 31% of all reported incidents, with Europe, and North America following at 28% and 25% according to IBM’s Security Threat Intelligence Index.
Although ‘all’ attacks are a concern, in the communications industry, the main cause for concern are man-in-the-middle attacks. This is where an attacker is able to eavesdrop on the data being sent back and forth between individuals or networks, by placing themselves between the sender and receiver, or the ‘man-in-the-middle’. From this position, the attacker is able to illicitly modify or otherwise access sensitive information before it reaches its destination.
Where this is a major concern is with public safety agency communications being intercepted. In the years before 2009, where encrypted communications were not as common as they are today, police communications were able to be discovered by ‘scanning’ for communications from two-way radios across an analogue network. In the modern day, public safety agencies use digital encrypted communications, where encrypted messages are broken up, sent over several frequencies and reassembled and decrypted at the receiving device.
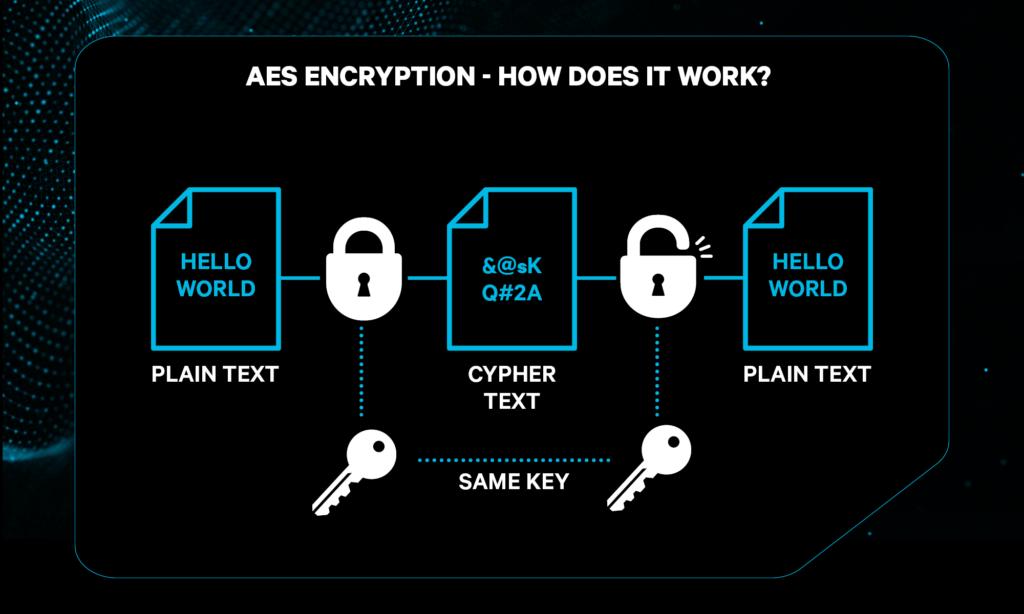
The modern industry standard for encryption is AES-256, this is currently one of the most secure encryption methods used in modern times. In basic terms, how does it work?
To read more about the intricacies of AES-256 encryption, see Kiteworks’ Risk Compliance Glossary.
AES-256 encryption is considered part of the ‘Advanced Encryption Standard’, it operates on 128-bit blocks of data using a 256-bit key. It undergoes multiple rounds of substitution, permutation (possible ways in which a set or number can be arranged), and mixing steps using the ’round key’. This process is repeated in several rounds (14 is the standard amount of rounds), ensuring security through confusion and diffusion.
With AES encryption, the process of ‘hacking’ a system or network becomes an almost unfeasible task that would take millions of years with current technology. Fundamentally, it’s a game of mathematical operations with a large key size; where attempts are made to ‘guess’ the correct key it is impossible, AES256 is currently uncrackable with cutting edge technology and considered ‘quantum resistant’.
AES-256 is one of the most secure encryption methods, having been uncrackable by hackers even today, it is used extensively by public safety agencies, government, military applications and financial institutions to secure important data and communications. It also serves as the key encryption method used by Tait Communications’ voice and data systems.
Why choose Tait Secure Voice and Data Systems?
All Tait platforms are built with security at their core to mitigate the risk of cyber-security threats. At Tait, we’re dedicated to providing truly flexible and scalable solutions tailored to your organization’s needs. From Tait Secure Voice and Data Systems you can expect:
- Secure networks – The latest Tait Networks provide industry best practices featuring HTTPS, VPN servers on node controller, virus scanners, and network monitoring tools
- Encryption for Secure Comms – Tait DMR supports encryption and user authentication. Tait P25 supports end-to-end, 256 bit AES encryption; Key Management Facility (KMF) and Key FIll Device (KFD) features
- Core Tait Network Security – Remote access to the core Tait network is via IP connection only, through Secure Shell (SSH) utilizing encrypted traffic
- Manage the security of your entire communications system – Tait EnableProtect Advanced System Key (ASK) provides you with layers of security, meaning no unauthorized users can interfere with your radio fleet.
- Tait’s services all comply with ISO 27001, ensuring peace of mind, with the highest information security management standards. So when you trust your information systems to Tait, your privacy and security are protected.
To explore Tait’s diverse range of secure communications systems, learn more on our website.
 Read the latest Tait blog on the same subject: New Resources Help Emergency Managers Prepare for Cyber Attacks
Read the latest Tait blog on the same subject: New Resources Help Emergency Managers Prepare for Cyber Attacks
Subscribe to the Tait Newsletter, to get stories like this sent directly to your inbox.




